Video
Protecting “Yourself” Online
ការពារខ្លួនអ្នកតាមប្រព័ន្ធអិុនធឺណេត វិដេអូខាងលើនេះគឺនឹងពន្យល់អ្នកអំពីគន្លឺះសំខាន់ៗ ក្នងការការពារខ្លួនអ្នកតាមប្រព័ន្ធអិុនធឺណេត ។
Read More »-

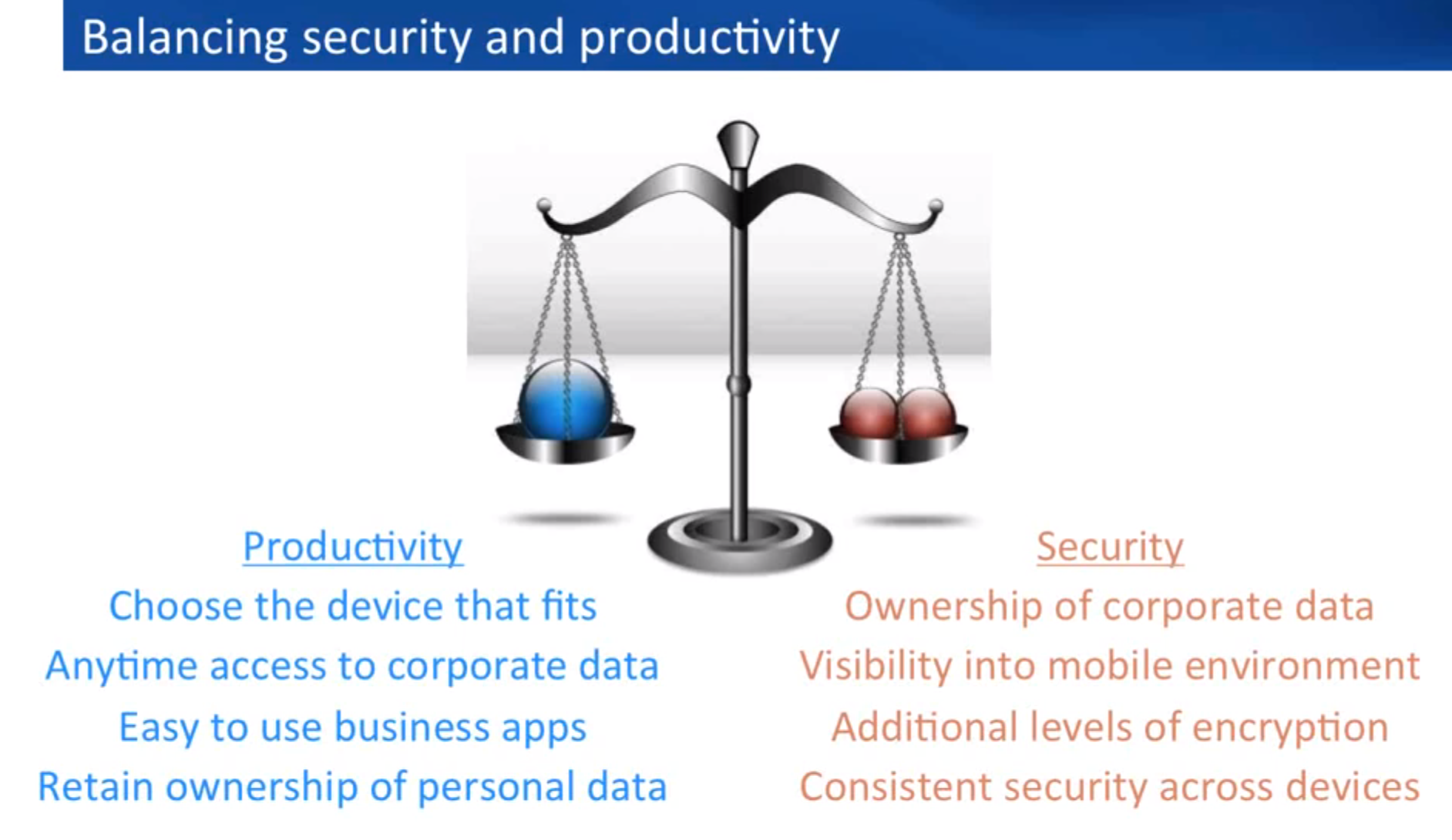
[Presentation] How to embrace BYOD by balancing mobile security and productivity
បង្ហាញស្តីពី BYOD ដោយការថ្លឹងថ្លែងពីសន្តិសុខឧបករណ៍ចល័ត និងផលិតកម្ម ខាងក្រោមនេះគឺជាជាបទបង្ហាញដោយអ្នកជំនាញស្តីអំពី Bring Your Own Device (BYOD)។ អ្នកជំនាញសន្តិសុខផ្នែកឧបករណ៍ចល័ត (Mobile Security Experts) បានបង្ហាញនូវព័ត៌មានថា ហេតុអ្វីបានជាក្រុមហ៊ុននានា មិនមាននូវគោលនយោបាយក្នុងការប្រើប្រាស់ឧបករណ័ចល័តផ្ទាល់ខ្លួន នៅក្នុងកន្លែងធ្វើការ។ សូមធ្វើការស្វែងយល់អំពីវិធីសាស្ត្រ ដែលអង្គភាពរបស់អ្នកអាចសម្រេចបាននូវការគ្រប់គ្រង…
Read More » -

[Presentation] Securing your health organization begins with encryption
បទបង្ហាញស្តីពី ការធ្វើឲ្យមានសន្តិសុខល្អចំពោះក្រុមហ៊ុនរបស់អ្នកដោយចាប់ផ្តើមចេញពីការបំលែង (Encryption) តើអង្គភាពរបស់អ្នកមានសន្តិសុខល្អហើយឬនៅ? សូមស្តាប់ការបកស្រាយពន្យល់ពីអ្នកអាជីព IT មកពីមន្ទីរពេទ្យពីរកន្លែង អំពីវិធីសាស្ត្រដែលគេប្រើប្រាស់នូវ ដំណោះស្រាយ encryption សម្រាប់ជួយធ្វើឲ្យមានសន្តិសុខល្អ នៅពេលដែលមានបញ្ហាសន្តិសុខកើតឡើង ហើយនិងកម្មវិធីកុំព្យូទ័រដែលប្រើប្រាស់ ដែលអ្នកធ្វើឲ្យអង្គភាពរបស់អ្នកទទួលសន្តិសុខល្អ ។
Read More » -

Offensive Computer Security 2014 [44 Parts]
វគ្គបណ្តុះបណ្តាលស្តីពីសន្តិសុខកុំព្យូទ័រ ២០១៤ គោលបំណងចំបងនៃអ្នកវាយប្រហារក្នុងការជ្រៀតចូល (exploit) ទៅក្នុងចំណុចខ្សោយ (vulnerability) គឺដើម្បីសម្រេចបានមកវិញនូវការប្រឹងប្រែងរបស់ខ្លួន (return on investment) ដែលជាទូទៅគឺពេលវេលារបស់ពួកគេ។ ការទទួលបានអ្វីមួយមកវិញនោះ គឺមិនមែនសំដៅតែទៅលើប្រាក់មួយមុខប៉ុណ្ណោះទេ អ្នកវាយប្រហារអាចមានការចាប់អារម្មណ៍ ក្នុងការទាញយកទិន្នន័យ អត្តសញ្ញាណ ឬក៏អ្វីផ្សេងទៀតដែលមានប្រយោជន័ដល់ពួគគេ។ ជំនាញក្នុងការធ្វើតេស្តវាយប្រហារ (penetration testing)…
Read More » Tip: Password Management
គន្លឺះក្នុងការគ្រប់គ្រងលើពាក្យសម្ងាត់ វិដេអូខាងលើនេះ នឹងបង្ហាញឬពន្យល់អ្នកអំពីវិធីសាស្ត្រក្នុងការគ្រប់គ្រងពាក្យសម្ងាត់ឬលេខសម្ងាត់ ប្រកបដោយប្រសិទ្ធិភាព។ សូមទស្សនាទាំងអស់គ្នា
Read More »Cyber Security for the Family – Internet Safety
សុវត្ថិភាពពេលចូលទៅកាន់អិុនធឺណែត វិដេអូខាងលើនេះ នឹងបង្ហាញអ្នកអំពីគន្លឹះក្នុងការការពារក្រុមគ្រួសារអ្នក ឲ្យចូលទៅកាន់បណ្តាញអិនធឺណែតប្រកបដោយសុវត្ថិភាព។ សូមទស្សនាទាំងអស់គ្នា!
Read More »CyberSecurity Tips For Your Computer
គន្លឹះសន្តិសុខល្អៗសម្រាប់ការពារកុំព្យួទ័ររបស់អ្នក វិដេអូឃ្លីបខាងលើនេះ នឹងផ្តល់ឲ្យអ្នកនូវគន្លឺះល្អក្នុងការជួយដល់ការ ការពារកុំព្យូទ័ររបស់អ្នក។ សូមទស្សនាទាំងអស់គ្នា!
Read More »Protecting Your Personal Information
ការពារព័ត៌មានផ្ទាល់ខ្លួនរបស់អ្នក វិដេអូខាងលើនេះ នឹងផ្តល់ឲ្យអ្នកនូវគន្លឺះខ្លីៗស្តីពីការការពារនូវព័ត៌មាននៅក្នុងកុំព្យូទ័ររបស់អ្នក។ សូមទស្សនាទាំងអស់គ្នា
Read More »-

Kali Linux Interview [Full]
កិច្ចសម្ភាសជាមួយនឹងអ្នកបង្កើត Kali Linux អ្នកអភិវឌ្ឍន៍ស្នូលនៃកម្មវិធី Kali Linux បានចូលរួមមកធ្វើការជជែកពិភាក្សាអំពីប្រវត្តិនៃគម្រោងមួយនេះ ហើយអ្វីដែលអាចធ្វើឲ្យ Kali Linux អាចឈរជើងបានយ៉ាងមាំ នៅក្នុងឧស្សាហកម្ម penetration, ជជែកពីអនាគត និងការយល់ខុសផ្សេងៗដែលគាត់ចង់ធ្វើការកែប្រែ។ ព្រមជាមួយគ្នានេះផងដែរ ពួកគាត់នឹងធ្វើការពន្យល់នូវការបញ្ចេញថ្មីៗទាំងអស់ មានដូចជា KDE ហើយនឹងការបង្ហាញពីជំនាន់ចុងក្រោយនៃ…
Read More » Introduction to Network Security
ការណែនាំអំពីសន្តិសុខបណ្តាញ វិដេអូខាងលើនេះ នឹងណែនាំឲ្យស្គាល់ថាតើអ្វីទៅជាសន្តិសុខបណ្តាញ? វាមានសារៈសំខាន់យ៉ាងដូចម្តេច? សូមទស្សនាទាំងអស់គ្នា
Read More »How-to Penetration Testing and Post Exploitation with Armitage and msfconsole
ការជ្រៀតចូលទៅក្នុងប្រព័ន្ធដោយប្រើប្រាស់ Armitage និង msfconsole នៅក្នុងវិដេអូខាងលើនេះ គឺបង្ហាញអ្នកអំពីវិធីសាស្ត្រក្នុងការជ្រៀតចូលទៅក្នុងប្រព័ន្ធដោយប្រើប្រាស់ Armitage និង msfconsole។ នៅក្នុងនោះមានការ បង្កើតនូវ Pivots, Meterpreter shells, Reporting, PSEXEC និង Pass-The-Hash attacks ។…
Read More »-

Top 5 Ways to Prevent a Cyber Attack
វិធីប្រាំយ៉ាងការពារការវាយប្រហារតាមអិនធឺណែត (Cyber Attack) វិដេអូខាងក្រោមនេះគឺបង្ហាញអ្នកពីវិធីសាស្ត្រទាំងប្រាំយ៉ាងក្នុងកិច្ចការពារការវាយប្រហារពីអិនធឺណែត (Cyber Attack)៖ 1. ផ្តល់ការអប់រំ-បណ្តុះបណ្តាលដល់បុគ្គលិករបស់អ្នក (educate your employees) 2. រើសបុគ្គលិកផ្នែកសន្តិសុខ (hire security) 3. បញ្ចូលកម្មវិធីកំចាត់មេរោគ (anti-malware) 4. សន្តិសុខចំពោះផ្នែករឹង…
Read More » -

How does hacker effect Cambodia Society
តើអ្នកវាយប្រហារតាមអិនធឺណែត (hackers) មានផលប៉ះពាល់ដល់សង្គមកម្ពុជាយ៉ាងដូចម្តេច? ខាងក្រោមនេះគឺជាវិដេអូឃ្លីបដែលបានដកស្រង់ចេញពីកិច្ចសន្ទនា នាថ្ងៃទី០៧ ខែមិថុនា ឆ្នាំ២០១៤ នៅស្ថានីយ៍ទូរទស្សន៍ CNC។ មានការជជែកពិភាក្សាគ្នាក្រោម ប្រធានបទ ថាតើអ្នកវាយប្រហារតាមប្រព័ន្ធអិនធឺណែត (hacker) មានផលប៉ះពាល់យ៉ាងដូចម្តេចចំពោះសង្គមកម្ពុជាបច្ចុប្បន្ន។ មានសំនួរមួយចំនួនត្រូវបានចោទសួរទៅកាន់វាគ្មិនកិត្តិយសទាំងបីរូប៖ ១. Hacker ល្អមានសមត្ថភាពខ្ពស់ តែសង្គមមិនផ្តល់ផលប្រយោជន៍ដល់គាត់ប៉ុន្មានទេ? តើមានវិធីសាស្ត្រយ៉ាងណា…
Read More » Phishing Indicators in 2 Minutes
យល់ដឹងពី Phising ក្នុងពេល ២នាទី Phishing (អានថា Fishing) គឺជាវិធីសាស្ត្រមួយប្រភេទដែលអ្នកវាយប្រហារ ធ្វើការបន្លំនូវឯកសារផ្សេងៗ ដោយផ្ញើរជាសារអេឡិចត្រូនិច ឬវិបសាយ ដើម្បីឲ្យអ្នកចុច ហើយបន្ទាប់មក អ្នកវាយប្រហារនឹងធ្វើការលួចព័ត៌មានពីអ្នក។ សូមទស្សនាទាំងអស់គ្នា ដើម្បីបានជាចំណេះដឹង!
Read More »